Are you interested in what Zama is and the way it’s shaping the way forward for blockchain expertise? In the event you’ve ever questioned why public blockchains wrestle with confidentiality, you’re not alone. Builders, companies, and regulators all face the identical rigidity between transparency and privateness, and that rigidity is driving rising consideration towards encrypted computation and the ZAMA token that helps this rising ecosystem.
On this article, you’ll study Zama’s distinctive strategy to fixing privateness challenges, its torus absolutely homomorphic encryption (FHE) expertise, and the way it powers purposes like personal stablecoins, confidential DeFi, and privacy-preserving AI. We’ll additionally discover the ZAMA token’s utility, its ecosystem, and the way it compares to different privateness applied sciences. Able to get into the main points? Learn on.
What Is Zama?
Zama is a privacy-focused blockchain infrastructure firm constructing the Zama Community to make confidential computing doable on public blockchains. In the event you perceive the blockchain fundamentals, you already know that transparency is each a power and a limitation. Zama works on the lacking layer by letting encrypted good contracts course of encrypted knowledge with out exposing it on-chain.
Zama reached a significant milestone by turning into the primary firm centered on absolutely homomorphic encryption to realize unicorn standing, following a funding spherical that introduced in $57 million. It crossed a valuation above $1 billion in June 2025, turning into the primary unicorn constructed fully round absolutely homomorphic encryption. That milestone adopted a powerful Sequence B funding spherical backed by Pantera Capital, signaling severe confidence from institutional crypto buyers.
Somewhat than making a closed system, the Zama Community goals to plug into current blockchains and developer workflows. This strategy helps groups construct confidential purposes that maintain balances, encrypted inputs, and logic personal whereas staying decentralized and verifiable. Zama positions itself on the intersection of privateness, compliance, and real-world blockchain adoption.


What Downside Does Zama Clear up?
Public blockchains expose buyer knowledge by design. Each stability, transaction element, and good contract enter sits in plain view, which creates severe limits for actual monetary, enterprise, and institutional use. Customers lose privateness, companies can not defend delicate logic, and regulators wrestle to assist compliant programs constructed on absolutely clear ledgers. This hole slows adoption and forces builders to decide on between decentralization and confidentiality.
Zama’s expertise addresses this drawback by permitting good contracts to compute immediately on encrypted knowledge. As a substitute of hiding exercise off-chain or counting on belief assumptions, purposes maintain data confidential whereas nonetheless operating on public networks. This strategy protects consumer balances, transaction quantities, and enterprise guidelines with out breaking composability or auditability.
With out native confidentiality, many use instances merely don’t work on-chain, together with personal funds, compliant id programs, and enterprise knowledge processing. Zama’s expertise removes this barrier and makes it doable to construct purposes that respect privateness whereas staying decentralized, verifiable, and usable at scale.
How Does Zama Work?
Zama operates utilizing absolutely homomorphic encryption (FHE), a groundbreaking technique that permits encrypted values to be processed with out decryption. This ensures that delicate data stays safe all through its complete lifecycle, even throughout computation.
The inspiration of Zama’s expertise lies in its core structure, which incorporates programmable bootstrapping. This function allows environment friendly and scalable encrypted computations, making it sensible for real-world purposes.
Encrypted knowledge sorts in encrypted good contracts additional improve privateness by permitting builders to construct safe purposes with out exposing buyer knowledge. Threshold decryption is one other key part, guaranteeing that solely licensed events can entry decrypted outcomes. This mixture of superior encryption methods and blockchain integration makes Zama a strong instrument for industries requiring excessive ranges of knowledge confidentiality, equivalent to finance, healthcare, and synthetic intelligence.
Absolutely Homomorphic Encryption (FHE) Defined


Absolutely homomorphic encryption permits computations to run immediately on encrypted values with out exposing the unique values at any level. For blockchain purposes, this removes the necessity to reveal balances, inputs, or enterprise logic simply to execute a sensible contract. The Zama Protocol makes use of FHE so purposes can course of delicate data on public networks whereas conserving that knowledge personal by default. This basis additionally opens the door for financial incentives, since safe computation creates new roles for validators and members, which is the place tokenomics might apply to Zama turns into related.
FHE alone shouldn’t be sufficient to assist actual purposes at scale. The confidentiality protocol should translate superior cryptography right into a system that builders can truly use, which leads immediately into how Zama buildings its core structure.
Zama Core Structure
The Zama Protocol combines FHE with blockchain execution to assist good contracts that function fully on encrypted knowledge. Builders work together with acquainted programming fashions, whereas the community handles encrypted computation, verification, and managed decryption. This construction permits privateness to coexist with decentralization and composability, and it additionally creates clear factors the place incentives and protocol charges can align with community utilization and safety.
1. Programmable Bootstrapping
Programmable bootstrapping refreshes encrypted circuits values throughout computation so contracts can run advanced logic with out shedding accuracy. Zama applies this method to assist conditional logic and repeated confidential operations inside good contracts. As utilization grows, this course of turns into a measurable useful resource, which helps clarify how tokenomics might apply to Zama by computation prices and community rewards.
2. Encrypted Information Sorts in Good Contracts
Zama offers encrypted knowledge sorts that behave like normal variables whereas conserving their contents hidden. Good contracts can retailer, evaluate, and replace these values with out ever revealing them on-chain. This function makes privateness native to software design and creates demand for safe execution, which might be priced and incentivized by the protocol’s financial mannequin.
3. Threshold Decryption
Threshold decryption splits decryption authority throughout a number of members so no single entity controls entry to delicate outcomes. Solely when a required group cooperates can the ultimate output be revealed. This design strengthens safety and helps decentralized belief, whereas additionally defining roles which will earn rewards, additional exhibiting how tokenomics might apply to Zama because the community matures.
Key Options of the Zama Protocol
As privateness strikes from a nice-to-have to an actual requirement, Zama focuses on constructing sensible instruments that builders and companies can truly use. The confidential protocol doesn’t deal with confidentiality as an add-on. It builds it immediately into how specialised good contract engines execute and work together. Listed below are the important thing options that outline the Zama Protocol and clarify why it stands out.
1. Native Encrypted Computation
Zama permits good contracts to compute immediately on encrypted knowledge. Encrypted inputs, states, and outputs stay confidential all through execution. This design removes the necessity to reveal delicate data simply to make use of a decentralized software, whereas nonetheless preserving correctness and verifiability on-chain.
2. Open-Supply Cryptographic Framework
The Zama Protocol follows an open supply cryptography firm mannequin, giving builders and researchers full visibility into its cryptographic elements. This strategy encourages audits, neighborhood contributions, and long-term belief. By conserving the core expertise open-source, Zama helps transparency on the protocol degree whereas defending consumer knowledge on the software degree.
3. Developer-Pleasant Good Contract Integration
Zama offers encrypted knowledge sorts and tooling that match into acquainted good contract workflows. Builders don’t want to revamp purposes from scratch to assist privateness. They’ll construct utilizing established patterns whereas the protocol handles encrypted computation behind the scenes.
4. Decentralized and Safe Decryption
The Zama protocol operates on a threshold-based mechanism to regulate how and when encrypted outcomes grow to be readable. No single participant can decrypt delicate knowledge alone. This construction reduces belief assumptions and aligns with decentralized safety ideas.
5. Composability With Current Blockchains
Zama designs its expertise to work alongside current blockchain networks moderately than changing them. Functions can stay interoperable whereas gaining compliant confidentiality, making it simpler to combine encrypted knowledge into broader decentralized ecosystems.
Benefits and Limitations of Zama (FHE)
Zama’s absolutely homomorphic encryption (FHE) expertise affords groundbreaking options for knowledge privateness and safety. Nevertheless, like every expertise, it comes with its personal set of benefits and limitations.
Benefits of Zama (FHE)
Enhanced Information Privateness: Zama ensures that delicate data stays encrypted all through its lifecycle, eliminating the danger of publicity throughout processing.Versatility Throughout Industries: The protocol is adaptable to numerous sectors, together with finance, healthcare, and synthetic intelligence, the place knowledge confidentiality is essential.Open-Supply Collaboration: Zama’s open-source framework fosters innovation and transparency, permitting builders to contribute and enhance the expertise.Scalability: The structure helps environment friendly and scalable encrypted computations, making it sensible for real-world purposes.
Limitations of Zama (FHE)
Computational Overhead: Absolutely homomorphic encryption requires vital computational sources, which might affect efficiency in sure situations.Complexity for Builders: Implementing FHE-based options might require specialised information, posing a studying curve for builders new to the expertise.Adoption Challenges: As a comparatively new expertise, FHE might face resistance from industries unfamiliar with its advantages or hesitant to undertake superior encryption strategies.
Zama Product Ecosystem
Zama Protocol: The inspiration of the ecosystem, develops absolutely homomorphic encryption (FHE) for safe and personal knowledge processing.ZAMA Token: Powers the ecosystem by facilitating transactions, incentivizing builders, and supporting governance inside the community.Developer Instruments: A collection of open-source instruments designed to assist builders combine FHE into their purposes seamlessly.Allows confidential Good Contracts: Allow the creation of decentralized purposes (dApps) that preserve consumer privateness and knowledge confidentiality.Zama Community: A sturdy infrastructure that helps encrypted computations and ensures scalability for real-world purposes.Ecosystem Partnerships: Collaborations with industries like DeFi, AI, and healthcare to drive adoption and innovation.
Zama Use Instances and Functions


As extra on-chain exercise entails actual customers, property, and organizations, privateness turns into important moderately than non-obligatory. Zama’s expertise allows purposes that want a compliant confidentiality layer with out giving up decentralization or auditability. The next are a few of the most necessary use instances rising throughout the Zama Community and the broader Zama ecosystem.
1. Confidential DeFi (Non-public Balances and Trades)
DeFi purposes expose consumer balances, positions, and buying and selling methods by default. Zama’s expertise permits protocols to cover balances and transaction particulars whereas nonetheless implementing guidelines and settlement logic on-chain. Merchants can defend delicate data with out counting on off-chain programs or trusted intermediaries.
2. Non-public Stablecoins and Funds
Stablecoins and cost programs typically require privateness for on a regular basis use and regulatory alignment. The Zama Community helps encrypted transfers and balances, enabling personal funds that also enable compliance checks and managed disclosures when required.
3. Privateness-Preserving AI
AI fashions rely upon giant volumes of delicate knowledge. Zama’s expertise permits encrypted knowledge to be processed immediately, making it doable to run AI computations with out exposing uncooked inputs. This strategy helps defend consumer underlying knowledge whereas supporting decentralized AI crypto workflows, making it central to most of the finest AI crypto tasks for decentralized purposes.
4. RWA Tokenization
Tokenizing real-world property typically entails confidential monetary and possession knowledge. The Zama ecosystem helps encrypted logic for asset administration, valuation, and transfers, making on-chain illustration of real-world property extra sensible and safe.
5. Identification and Compliance Techniques
Identification programs should stability privateness with verification. Zama’s expertise allows encrypted id attributes that may be checked with out revealing underlying private data. This design helps regulatory compliance whereas respecting consumer privateness.
6. Enterprise and Healthcare Information Processing
Enterprises and healthcare suppliers handle extremely delicate knowledge that can not be made public. The Zama Community permits encrypted web knowledge processing for analytics, billing, and document administration, making blockchain viable for industries that require a strict confidentiality layer.
ZAMA Token Overview
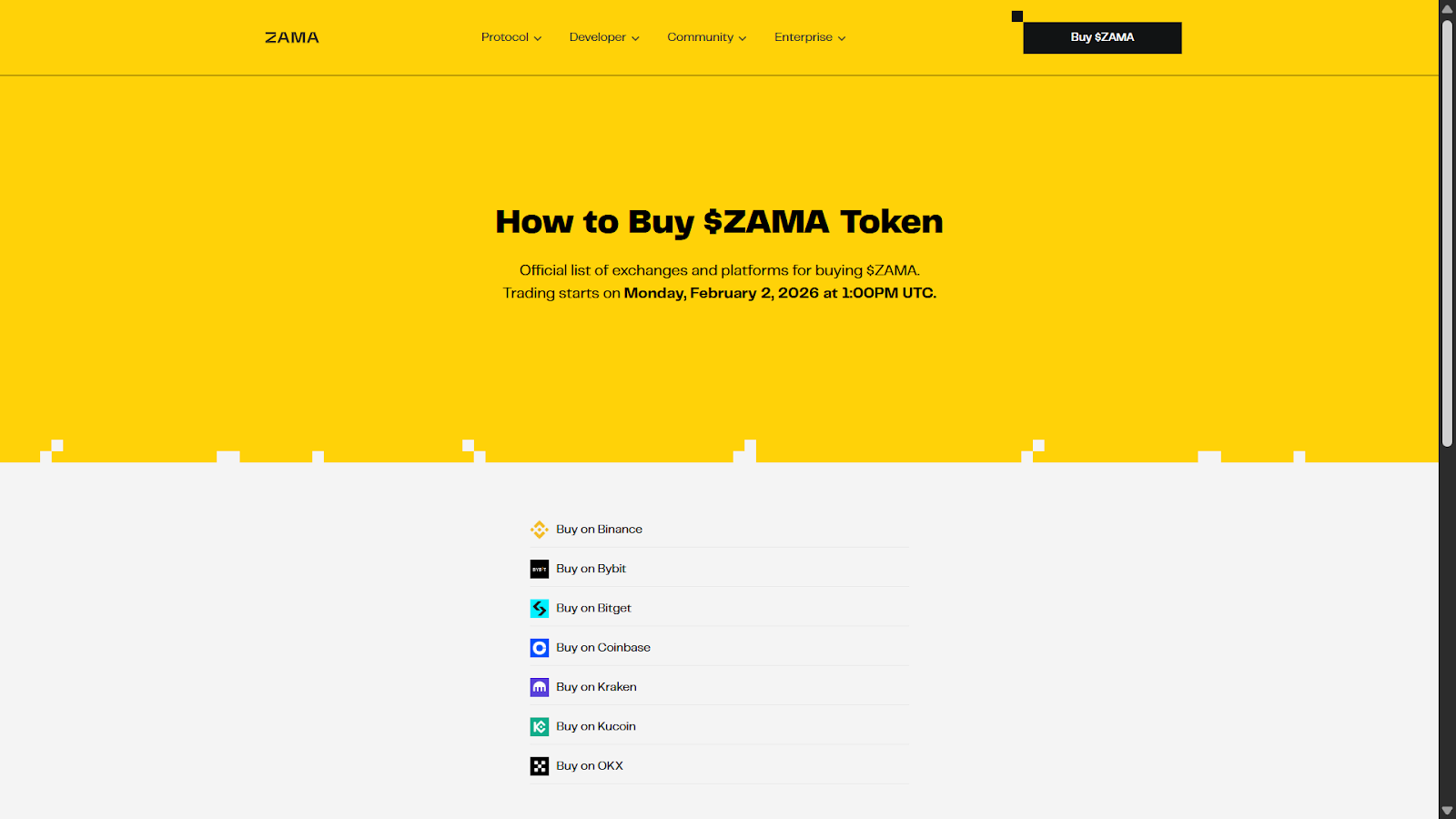



The ZAMA token performs a central position in supporting the privateness applied sciences in crypto that outline Zama’s ecosystem. It serves as a key part in driving adoption, incentivizing participation, and guaranteeing the community’s sustainability. The next are the primary facets of the ZAMA token:
Token Utility
The ZAMA token powers the ecosystem by facilitating transactions, enabling governance, and incentivizing builders to construct privacy-preserving purposes. It ensures that members can seamlessly work together inside the Zama Community whereas sustaining knowledge confidentiality.
Emissions and Incentives
Zama’s tokenomics embrace a well-structured emissions plan designed to reward early adopters and contributors. Incentives are distributed to builders, validators, and different members who actively assist the expansion and safety of the community.
Distribution Mannequin
The token distribution mannequin ensures a balanced allocation between stakeholders, together with the neighborhood, builders, and buyers. This strategy promotes decentralization and long-term sustainability whereas fostering belief inside the ecosystem.
Zama vs Different Privateness Applied sciences
Zama’s expertise stands out within the realm of privacy-preserving decentralized purposes, providing distinctive benefits over different privateness options. The next comparisons spotlight how Zama differs from different main applied sciences by way of performance, scalability, and safety.
Zama vs Zero-Data Proofs (ZKPs)
FeatureZamaZero-Data Proofs (ZKPs)Information ProcessingProcesses encrypted knowledge immediatelyVerifies knowledge with out revealing itScalabilityExcessive scalability for advanced computationsRestricted scalability for big datasetsUse InstancesBroader purposes in AI, DeFi, and extraPrimarily used for transaction privateness
Zama vs Safe Multi-Celebration Computation (MPC)
FeatureZamaSecure Multi-Celebration Computation (MPC)Information Dealing withProcesses encrypted knowledge independentlyRequires a number of events to collaborateEffectivityExtra environment friendly for single-party confidential operationsGreater overhead resulting from multi-party setupFunctionsExcellent for privacy-preserving dAppsRestricted to collaborative computations
Zama vs Trusted Execution Environments (TEE)
FeatureZamaTrusted Execution Environments (TEE)Safety MannequinDepends on encryption for privatenessDepends on hardware-based safetyFlexibilitySoftware program-based, adaptable to numerous use instances{Hardware}-dependent, much less versatileBelief NecessitiesNo reliance on {hardware} producersRequires belief in {hardware} suppliers
Zama Roadmap and Future Improvement
The Zama ecosystem is poised for vital development, with a transparent roadmap that focuses on advancing privacy-preserving applied sciences and increasing its purposes. Upcoming developments embrace enhancements to the absolutely homomorphic encryption sensible framework, making it much more environment friendly and scalable for real-world use instances. Plans to combine with extra blockchain networks goal to broaden the attain of Zama’s expertise, fostering adoption throughout various industries.
Efforts to strengthen developer instruments and sources will empower the neighborhood to construct revolutionary privacy-preserving decentralized purposes. Strategic partnerships with key gamers in sectors like DeFi, AI, and healthcare are anticipated to drive additional innovation and collaboration. The roadmap displays Zama’s dedication to creating a strong and sustainable ecosystem that prioritizes knowledge privateness and safety whereas enabling transformative options.
Conclusion
Zama’s expertise affords a groundbreaking strategy to knowledge privateness and safety, making it a priceless resolution for industries that deal with delicate data. Its absolutely homomorphic encryption sensible, open-source framework, and versatile purposes place it as a frontrunner in privacy-preserving decentralized purposes. The Zama ecosystem offers the instruments and infrastructure wanted to drive innovation whereas guaranteeing compliance and confidentiality. This mixture of superior expertise and sensible usability makes Zama a really perfect alternative for organizations in search of to undertake safe and scalable blockchain options.
FAQs
Is Zama a blockchain or a protocol?
Zama confidential blockchain protocol, not a standalone blockchain. It offers a completely homomorphic encryption (FHE) framework that may combine with current blockchain networks to allow privacy-preserving computations.
Does Zama have a local token?
Sure, Zama has a local token referred to as the ZAMA token. It powers the Zama ecosystem by facilitating transactions, incentivizing builders, and supporting governance inside the community.
What’s Zama used for?
Zama is used for enabling privacy-preserving decentralized purposes throughout varied industries. Its purposes embrace confidential DeFi, personal stablecoins, privacy-preserving AI, RWA tokenization, id programs, and safe enterprise knowledge processing.
How is Zama completely different from ZK privateness tasks?
Zama is completely different from ZK privateness tasks as a result of it makes use of absolutely homomorphic encryption (FHE) to course of encrypted knowledge immediately, whereas ZK tasks concentrate on verifying knowledge with out revealing it. This makes Zama extra versatile for advanced computations and broader use instances.









